Table of Contents
About
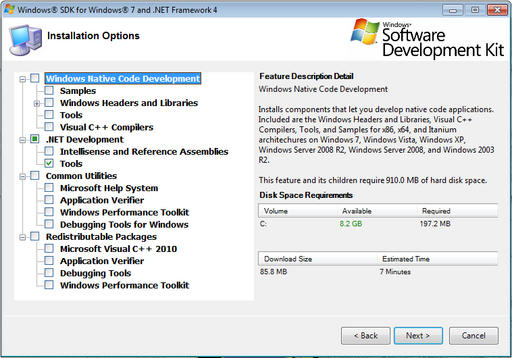
.NET supports HTTPs for HttpListener, but in order to use HTTPs, SSL certificates have to be installed and then bound to the IP and port pair of the listening application. You will need to download the Windows SDK in order to have access to the makecert.exe program. You will only need to install the .NET Tools from the Windows SDK, so you may want to disable all the other options.
Setting up Certificates
You will need to open-up a command prompt (press Windows+R and type cmd) and then change the path to where the Windows SDK tools were installed:
cd C:\Program Files\Microsoft SDKs\Windows\v7.1\bin
Note that this path may change depending on your machine.
Now, for the command-line part, the steps are as follows:
- Create a certificate authority using the command prompt, for example:
makecert -n "CN=CorradeCA" -r -sv CorradeCA.pvk CorradeCA.cer
where CorradeCA is the name of certificate authority - it can be any name, just make sure you are consistent when renaming CorradeCA to whatever you want because it will be referenced in the next step.
You will be prompted for a password and you can select None.
- Now, create an SSL certificate:
makecert -sk CorradeSignedByCA -iv CorradeCA.pvk -n "CN=CorradeSignedByCA" -ic CorradeCA.cer CorradeSignedByCA.cer -sr localmachine -ss My
where CorradeSignedByCA is the name of the SSL certificated signed by the certificate authority we have created previously - again, it can be any name, just use it consistently.
Installing Certificates
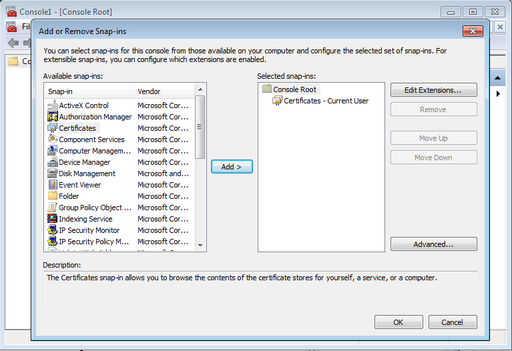
Now we have to install the certificates in the Trusted Authority store and the Personal store. In order to do this, open-up MMC (press Windows+R and type mmc) and go to File->Add/Remove Snap-in.... A list should pop up and you should select Certificates and press Add >. A window will pop-up asking for which account should the snap-in manage certificates for and you should select My user account.
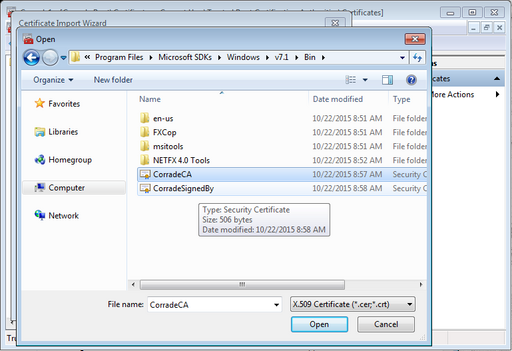
Next, go to Certificates - Current User->Trusted Root Certificates-Certificates and select the menu item Action->All Tasks->Import.... You will be greeted by a wizard and on the second page you will be prompted to specify a location to the certificate to install. You will have to browse to C:\Program Files\Microsoft SDKs\Windows\v7.1\bin or wherever you ran the makecert program.
You will have to select CorradeCA.cer which we generated previously using makecert:
and then click Open and when you get back to the wizard select Next > and accept all the default options. You will finally be prompted that Windows cannot validate this CA and that you should confirm it. Select Yes to accept to install CorradeCA.cer and you should see The import was successful.
Now we have to do the same for the SSL certificate. So, go back to MMC and go to Console Root->Certificates - Current User->Personal and then select the menu item Action->All Tasks->Import.... You will be prompted by the same wizard again so this time select CorradeSignedBy.cer. Now follow the wizard to the end with Next > and accept all the default options.
Bind Certificates
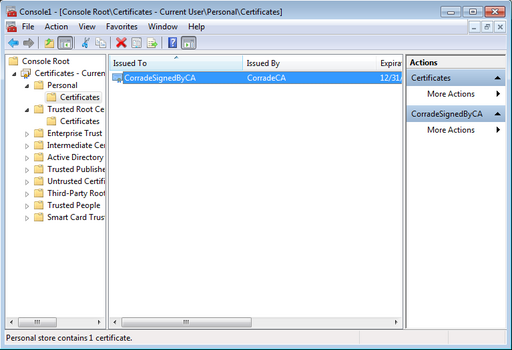
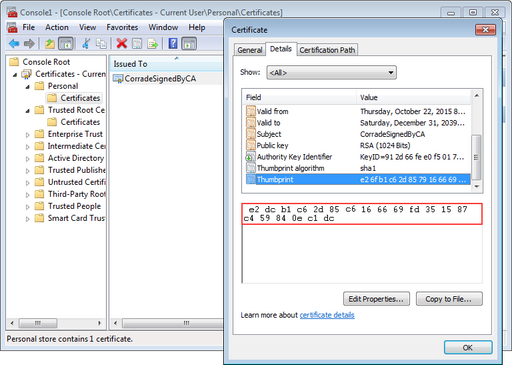
The final step is to bind the created certificate to the IP and port that you want the application to listen for HTTPs connections on. We first have to note down the thumbprint of the SSL certificate, so navigate to the personal certificate store:
and double-click CorradeSignedByCA and then go to the Details tab and select Show-><All>. Somewhere down the list of properties, you will find Thumbprint. You will need to jot that number down because we will need it later.
In this example it reads: e2dcb1c62d85c6166669fd351587c459840ec1dc which we will use to bind the certificate to the IP and port that the HttpListener is listening on. We thus change the prefix that the application listens on to use HTTPs instead of HTTP:
https://+:8080/
For the final step, we bind the IP and port pair using netsh. To do that, open a command prompt again (press Windows+R and type cmd) and type the following but change the parameters accordingly:
netsh http add sslcert ipport=0.0.0.0:8080 certhash=e2dcb1c62d85c6166669fd351587c459840ec1dc appid={d8bb7314-d9bc-48b4-bdb9-c93c04cf70bb}
where:
ipportis the IP and port pair that the .NET HttpListener listens on. Remember that+stands for any, such that the IP is0.0.0.0. Since the application will be listening on port8080, the result is0.0.0.0:8080.- the
certhashvalue is the thumbprint you noted before (in this example,e2dcb1c62d85c6166669fd351587c459840ec1dc). appidis the application UUID which can usually be retrieved fromAssemblyInfo.cs, for example, for Corrade the application UUID isd8bb7314-d9bc-48b4-bdb9-c93c04cf70bb.
If all goes well, you will see the message SSL Certificate successfully added and you are ready to use HttpListener over HTTPs.
For the contact, copyright, license, warranty and privacy terms for the usage of this website please see the contact, license, privacy, copyright.