Table of Contents
About
Unfortunately, retro console binders such as retroarch do not benefit of an API that would allow programmers to hook into the platform in order to observe the inner-workings of the engine. Furthermore, retroarch is fairly tacit when it comes to debugging and even enabling the most verboose logging does not mention any details about connecting clients.
Previous attempts to pull data on connecting netplay clients have resulted in python being a requirement, that is unfortunately not compatible with closed systems such as Lakka, as well as dropping down to bash scripting and using the Linux subsystem to retrieve the connecting IP address but without the ability to additionally obtain the nickname of the connecting client.
The following document describes a mechanism to obtain both the nickname of the connecting client matched by their IP address and then broadcast that information to a Node-Red instance that will have the responsibility of storing and displaying the connecting players on the world map.
Reverse-Engineering
It becomes clear that hinging on retroarch or closed-systems such as Lakka to provide such information is unreasonable such that the best course of action seems to drop down to packet interception in order to decode incoming traffic by relying on the netplay protocol definitions.
Via the documentation, it seems that once a netplay server receives a client, the very first thing that happens is that a handshake takes place along the following lines:
- send connection header
- receive and verify connection header
- send nickname
- receive nickname
The protocol can be observed trivially using tcpdump:
tcpdump -w netplay_connect.pcap -X -i br0 tcp port 55435
where:
netplay_connect.pcapis a PCAP packet capture file to be analyzed later,-Xdumps the data in ASCII format,-i br0monitors an interface, in this case, the network bridge over which traffic to the machine running netplay takes place,tcp port 55435makestcpdumplisten on the default netplay port55435
In order to observe the traffic, two machines are started, one retroarch instance acting as a client and another retroarch instance acting as a client while tcpdump sniffs and dumps packets whilst observing the traffic between the two retroarch instances.
Looking through the exchanged packets, very early on in the transmission, the following data is to be observed:
0000 7e 18 17 ed bc 76 38 63 bb 2c 51 b4 08 00 45 00 ~....v8c.,Q...E. 0010 00 50 06 06 40 00 40 06 6f d7 ac 10 01 51 4f 73 .P..@.@.o....QOs 0020 c7 f6 bd 39 d8 8b f5 07 6a 83 55 39 69 5b 50 18 ...9....j.U9i[P. 0030 01 00 f3 69 00 00 00 00 00 20 00 00 00 20 73 68 ...i..... ... sh 0040 65 6e 69 73 00 00 00 00 00 00 00 00 00 00 00 00 enis............ 0050 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ..............
where shenis is the nickname of the connecting retroarch client.
Leaving the header aside and observing the payload that includes the nickname shenis, the following bytes can be laid out in order:
00 00 00 00 00 20 00 00 00 20 73 68 65 6e 69 73 ...
+ + + +
| | | |
+---+ +---------------+
NETPLAY_CMD_NICK shenis
where it turns out that the sequence 0x0020 matches the netplay NICK command that sends the nickname of the connecting client. As it turns out, this 40 byte packet is well-defined within the netplay_private.h header of the retroarch netplay source code and corresponds to the NICK command.
Given the former, it seems that all that is left to do is to interactively sniff traffic from the outside world and to the machine running the netplay server while looking for a 40 byte packet that contains the 0x0020 marker that corresponds to the NICK netplay command. Once the packet is captured, the IP address of the connecting client is already known via the IP protocol and the nickname is contained within the rest of the 40 byte packet.
Engineering
The whole system will consist in a node.js script that shall be ran on the router in order to intercept TCP/Ip netplay traffic, extract the packet and send the nickname and IP address pair to an MQTT server. Node-Red and dataflow programming will be leveraged in order to subscribe to the MQTT server and receive the data sent by the node.js script in order to perform a geographic lookup of the IP address and then display the results on a rendered world map.
Netplay Sniffer
The netplay sniffer can be downloaded as a project from the Wizardry and Steamworks SVN by issuing the command:
svn co https://svn.grimore.org/netplaySniff
Once retrieved, the following command must be used in order to install all dependencies:
npm install
This will require the pcap library development files to be installed (on Debian, the libpcap-dev package should be installed before running npm install).
The next step is to configure the netplaySniff project by copying config.yml.dist to config.yml and then editing the file accordingly. The YAML file contains documentation that should provide enough guidance.
In order to test, the project can be started by making main.js executable and then running main.js.
If everything goes well, the project can be demonized on SystemD by copying the file netplaySniff.service from contrib/linux/systemd/ into /etc/systemd/system and then enabling the netplaySniff.service using systemd.
Code
Here is the code for the netplaySniff project and the configuration file config.yml.
netplaySniff
#!/usr/bin/env node /////////////////////////////////////////////////////////////////////////// // Copyright (C) 2024 Wizardry and Steamworks - License: MIT // /////////////////////////////////////////////////////////////////////////// const fs = require('fs') const path = require('path') const { createLogger, format, transports } = require('winston') const mqtt = require('mqtt') const YAML = require('yamljs') const Cap = require('cap').Cap const decoders = require('cap').decoders const PROTOCOL = decoders.PROTOCOL const crypto = require('crypto') const { exec } = require("child_process") const Inotify = require('inotify-remastered').Inotify const inotify = new Inotify() const sqlite = require('sqlite3') const { Command } = require('commander') // set up logger const logger = createLogger({ format: format.combine( format.timestamp({ format: 'YYYYMMDDHHmmss' }), format.printf(info => `${info.timestamp} ${info.level}: ${info.message}` + (info.splat !== undefined ? `${info.splat}` : " ") ) ), transports: [ new transports.Console({ timestamp: true }), new transports.File( { timestamp: true, filename: path.join(path.dirname(fs.realpathSync(__filename)), 'log/netplaySniff.log') } ) ] }) const program = new Command() program .name('netplaySniff') .description(` +--+ | | Monitor netplay traffic, sniff users and their | || | IP addresses and store them in a database. +--+ `) .version('1.0') program .command('run') .option('-c, --config <path>', 'path to the configuration file', 'config.yml') .option('-d, --database <path>', 'the path where to store a database', 'db/players.db') .description('run the program as a daemon') .action((options) => { logger.info(`running as a daemon with configuration from ${options.config} and database at ${options.database}`) // load configuration file. var config = YAML.load(options.config) // Watch the configuration file for changes. inotify.addWatch({ path: options.config, watch_for: Inotify.IN_MODIFY, callback: function (event) { logger.info(`Reloading configuration file config.yml`) config = YAML.load(options.config) } }) const mqttClient = mqtt.connect(config.mqtt.connect) mqttClient.on('reconnect', () => { logger.info('Reconnecting to MQTT server...') }) mqttClient.on('connect', () => { logger.info('Connected to MQTT server.') // Subscribe to group message notifications with group name and password. mqttClient.subscribe(`${config.mqtt.topic}`, (error) => { if (error) { logger.info('Error subscribing to MQTT server.') return } logger.info('Subscribed to MQTT server.') }) }) mqttClient.on('close', () => { logger.error('Disconnected from MQTT server.') }) mqttClient.on('error', (error) => { logger.error(`MQTT ${error}`) console.log(error) }) // set up packet capture logger.info(`setting up packet capture`) const cap = new Cap() const filter = `tcp and dst port ${config.netplay.port}` const bufSize = 10 * 1024 * 1024 const buffer = Buffer.alloc(65535) var device = Cap.findDevice(config.listen); const linkType = cap.open(device, filter, bufSize, buffer) cap.setMinBytes && cap.setMinBytes(0) cap.on('packet', () => { let netplay = {} if (linkType !== 'ETHERNET') { return } var ret = decoders.Ethernet(buffer) if (ret.info.type !== PROTOCOL.ETHERNET.IPV4) { return } ret = decoders.IPV4(buffer, ret.offset) netplay.src = ret.info.srcaddr netplay.dst = ret.info.dstaddr if (ret.info.protocol !== PROTOCOL.IP.TCP) { return } var dataLength = ret.info.totallen - ret.hdrlen ret = decoders.TCP(buffer, ret.offset) dataLength -= ret.hdrlen var payload = buffer.subarray(ret.offset, ret.offset + dataLength) // look for the NETPLAY_CMD_NICK in "netplay_private.h" data marker. if (payload.indexOf('0020', 0, "hex") !== 2) { return } // remove NULL and NETPLAY_CMD_NICK netplay.nick = payload.toString().replace(/[\u0000\u0020]+/gi, '') var shasum = crypto.createHash('sha1') shasum.update(`${netplay.nick}${netplay.src}`) netplay.hash = shasum.digest('hex') netplay.time = new Date().toISOString() logger.info(`Player ${netplay.nick} joined via IP ${netplay.src}`); const db = new sqlite.Database(config.db.file, sqlite.OPEN_CREATE | sqlite.OPEN_READWRITE | sqlite.OPEN_FULLMUTEX, (error) => { if (error) { logger.error(`failed to open database: ${config.db.file}`) return } db.run(`CREATE TABLE IF NOT EXISTS "players" ("hash" TEXT(40) NOT NULL PRIMARY KEY, "nick" TEXT(15) NOT NULL, "ip" TEXT NOT NULL, "date" TEXT NOT NULL)`, (error, result) => { if (error) { logger.error(`could not create database table: ${error}`); return } db.run(`REPLACE INTO "players" ("hash", "nick", "ip", "date") VALUES ($hash, $nick, $ip, DateTime('now'))`, { $hash: netplay.hash, $nick: netplay.nick, $ip: netplay.src }, (error) => { if (error) { logger.error(`could not insert player and IP into database: ${error}`) return } logger.info(`player added to database`) }) }) }) // send data to MQTT server const data = JSON.stringify(netplay, null, 4) mqttClient.publish(config.mqtt.topic, data, (error, packet) => { logger.info(`player data sent to MQTT broker`) }) // ban by nick. let nickBanSet = new Set(config.bans.nicknames) if (nickBanSet.has(netplay.nick)) { logger.info(`nick found to be banned: ${netplay.nick}`) exec(`/usr/sbin/iptables -t mangle -A PREROUTING -p tcp --src ${netplay.src} --dport ${config.netplay.port} -j DROP`, (error, stdout, stderr) => { if (error) { logger.error(`Error returned while banning connecting client ${error.message}`) return } if (stderr) { logger.error(`Standard error returned ${stderr}`) return } if (stdout) { logger.info(`Standard error reported while banning ${typeof stdout}`) return } }) } }) }) program.parse()
config.yml
########################################################################### ## Copyright (C) 2023 Wizardry and Steamworks - License: MIT ## ########################################################################### # beware that all configuration settings might end up overriden by the # # specific command-line options passed to the daemon # ########################################################################### # The local IP address of the router that this script is running on. listen: 192.168.1.1 # The MQTT connection string. mqtt: connect: "mqtt://iot.lan" topic: "arcade/netplay/clients" netplay: # the netplay port (the default is 55435), # this can vary depending on emulator port: 55435 # where to store the database file db: file: "db/players.db" # Various bans that can be placed on connecting clients. bans: nicknames: - Cain
Node-Red
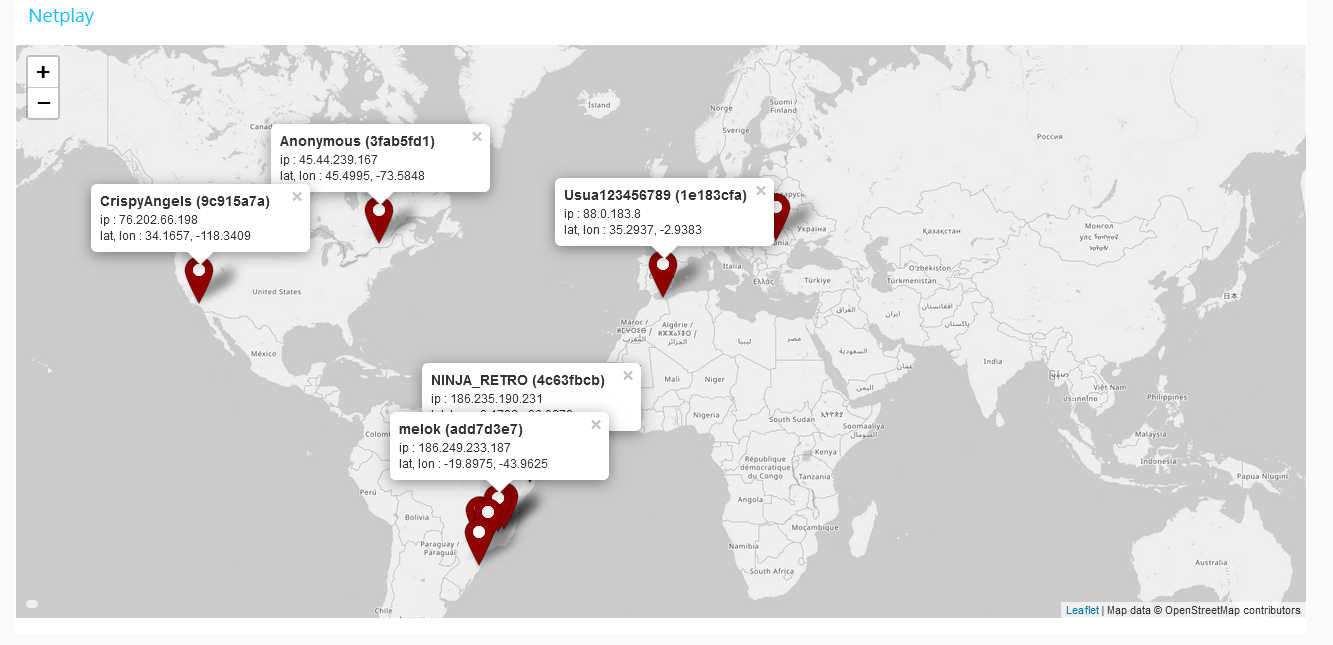
Using Node-Red the following plot is obtained by accumulating the IP and nickname tuples during an evening when a retroarch instance has been left to host a game:
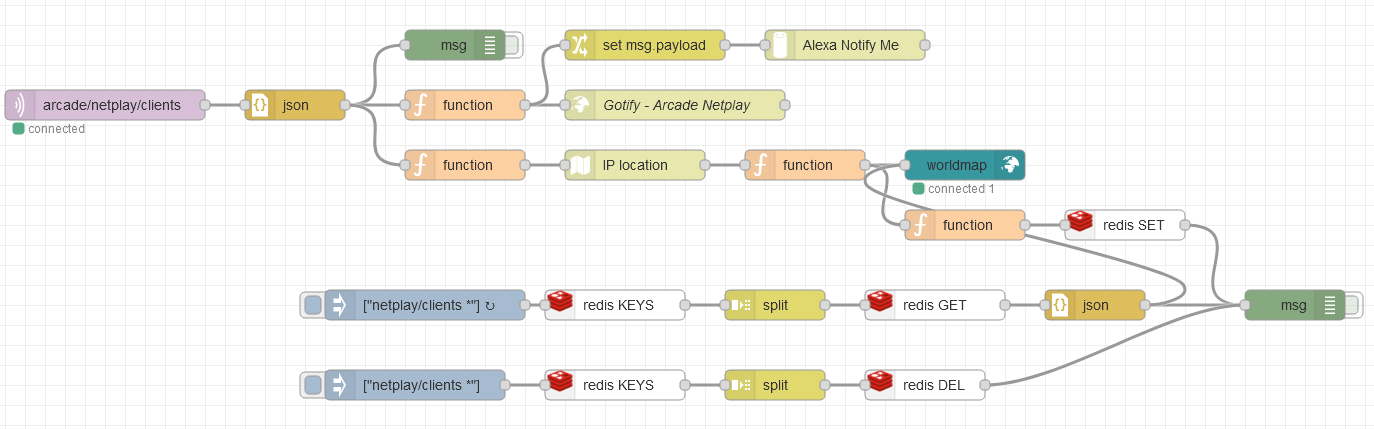
The corresponding Node-Red flow is a little complicated yet should be robust enough to foresee any problems that might occur. Here is an overview of the Node-Red flow:
In short, the following steps take place, in order:
- Node-Red subscribes to the MQTT broker on the topic
arcade/netplay/clientsand listens for JSON data sent by thenetplaySnifferscript running on the router (purple left-most box labeledarcade/netplay/clients), - the JSON data is converted to a JavaScript object and the IP address is sent through a geoip locator (
IP locationbox), - the first function after the IP geolocator sends the data to the UI world map (green box labeled
worldmap) whilst the second function sends the data to a Redis server running on the local machine for storage
The netplaySniff node.js script sends the connecting IP address and nickname by sniffing the packets exchanged during the netplay handshake but also additionally generates a Bernstein "times 33" hash, by combining the nickname and the IP address, that is conveniently short. The hash is created in order to mitigate the situation where connecting clients do not have a nickname set such that the nickname is by default set to Anonymous or the situation where two people have the same nickname but a different IP address. Furthermore, the hash itself is used as the key when storing the whole structure in Redis such that the same nickname and IP pair will always update the datapoint, whilst any variance of nickname or IP will generate a new datapoint to be plotted on the map.
On the lower side of the Node-Red flow, there are two distinct lines, the upper that can be triggered both manually and is triggered every time Node-Red restarts which is responsible for re-populating the world map in case the Node-Red machine restarts by retrieving the data from Redis, whilst the lower line can be used to delete all the stored data pertaining to the netplay clients thereby resetting both the data and the world map.
The data is stored within redis, but the netplaySniff node.js script also saves the data to a database. The database for the netplaySniff script is indexed by a hash that is composed of the nickname and the IP address allowing for multiple players per IP in order to account for carrier grade NAT and allow plotting more connecting people on a map.
Flow Export
[{"id":"ae949abd73ceac19","type":"group","z":"3761db287decc539","name":"Netplay Connecting Clients","style":{"label":true},"nodes":["72fc116f8e2618f5","f2cb5e812d118ced","fd8c9a54bcea4983","12546369696342e6","c3d9a185c86ef268","2459acaa8e49e279","e383d4f6430a364b","ab38609e87589496","9876a5a6697bfd06","57889c6c2fbcfb73","55996f191cfcda2b","9cb9e20bf8575aa8","6fad5908543d2dad","05fcd4a5909455c0","5835800109b76ff2","eb5d222becc3522b","38e3e6f23b0fc946","aedc78b740f89677","f857c585aa7661f8"],"x":54,"y":699,"w":1352,"h":362},{"id":"72fc116f8e2618f5","type":"ui_worldmap","z":"3761db287decc539","g":"ae949abd73ceac19","group":"5851d6200ca81d40","order":1,"width":0,"height":0,"name":"","lat":"","lon":"","zoom":"","layer":"OSMG","cluster":"","maxage":"600","usermenu":"hide","layers":"show","panit":"false","panlock":"false","zoomlock":"false","hiderightclick":"true","coords":"none","showgrid":"false","showruler":"false","allowFileDrop":"false","path":"/worldmap","overlist":"TL","maplist":"OSMG","mapname":"","mapurl":"","mapopt":"","mapwms":false,"x":1160,"y":800,"wires":[]},{"id":"f2cb5e812d118ced","type":"mqtt in","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","topic":"arcade/netplay/clients","qos":"2","datatype":"auto","broker":"331ec98c048042f6","nl":false,"rap":true,"rh":0,"inputs":0,"x":180,"y":800,"wires":[["fd8c9a54bcea4983"]]},{"id":"fd8c9a54bcea4983","type":"json","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","property":"payload","action":"","pretty":false,"x":370,"y":800,"wires":[["c3d9a185c86ef268"]]},{"id":"12546369696342e6","type":"function","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","func":"msg.payload = { \n \"name\": `${msg.data.nick} (${msg.data.hash.slice(0, 3)}...)`, \n \"src\": msg.data.src,\n \"dst\": msg.data.dst,\n \"time\": msg.data.time,\n \"lat\": msg.payload.ll[0], \n \"lon\": msg.payload.ll[1],\n \"icon\": \":raised_hand:\"\n}\n\nreturn msg\n","outputs":1,"timeout":"","noerr":0,"initialize":"","finalize":"","libs":[],"x":1000,"y":800,"wires":[["72fc116f8e2618f5","f857c585aa7661f8"]]},{"id":"c3d9a185c86ef268","type":"function","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","func":"msg.data = msg.payload\nmsg.payload = msg.data.src\nreturn msg\n","outputs":1,"timeout":"","noerr":0,"initialize":"","finalize":"","libs":[],"x":520,"y":800,"wires":[["38e3e6f23b0fc946"]]},{"id":"2459acaa8e49e279","type":"redis-command","z":"3761db287decc539","g":"ae949abd73ceac19","server":"4475d6f04474e5ef","command":"KEYS","name":"","topic":"","params":"[]","paramsType":"json","payloadType":"json","block":false,"x":450,"y":940,"wires":[["9876a5a6697bfd06"]]},{"id":"e383d4f6430a364b","type":"redis-command","z":"3761db287decc539","g":"ae949abd73ceac19","server":"4475d6f04474e5ef","command":"SET","name":"","topic":"","params":"[]","paramsType":"json","payloadType":"json","block":false,"x":1320,"y":740,"wires":[[]]},{"id":"ab38609e87589496","type":"inject","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","props":[{"p":"payload"},{"p":"topic","vt":"str"}],"repeat":"600","crontab":"","once":true,"onceDelay":0.1,"topic":"","payload":"[\"netplay/clients *\"]","payloadType":"json","x":260,"y":940,"wires":[["2459acaa8e49e279"]]},{"id":"9876a5a6697bfd06","type":"split","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","splt":"\\n","spltType":"str","arraySplt":1,"arraySpltType":"len","stream":false,"addname":"payload","x":610,"y":940,"wires":[["57889c6c2fbcfb73"]]},{"id":"57889c6c2fbcfb73","type":"redis-command","z":"3761db287decc539","g":"ae949abd73ceac19","server":"4475d6f04474e5ef","command":"GET","name":"","topic":"","params":"[]","paramsType":"json","payloadType":"json","block":false,"x":770,"y":940,"wires":[["55996f191cfcda2b"]]},{"id":"55996f191cfcda2b","type":"json","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","property":"payload","action":"","pretty":false,"x":930,"y":940,"wires":[["72fc116f8e2618f5"]]},{"id":"9cb9e20bf8575aa8","type":"redis-command","z":"3761db287decc539","g":"ae949abd73ceac19","server":"4475d6f04474e5ef","command":"KEYS","name":"","topic":"","params":"[]","paramsType":"json","payloadType":"json","block":false,"x":450,"y":1020,"wires":[["05fcd4a5909455c0"]]},{"id":"6fad5908543d2dad","type":"inject","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","props":[{"p":"payload"},{"p":"topic","vt":"str"}],"repeat":"","crontab":"","once":false,"onceDelay":0.1,"topic":"","payload":"[\"netplay/clients *\"]","payloadType":"json","x":250,"y":1020,"wires":[["9cb9e20bf8575aa8"]]},{"id":"05fcd4a5909455c0","type":"split","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","splt":"\\n","spltType":"str","arraySplt":1,"arraySpltType":"len","stream":false,"addname":"payload","x":610,"y":1020,"wires":[["5835800109b76ff2"]]},{"id":"5835800109b76ff2","type":"redis-command","z":"3761db287decc539","g":"ae949abd73ceac19","server":"4475d6f04474e5ef","command":"DEL","name":"","topic":"","params":"[]","paramsType":"json","payloadType":"json","block":false,"x":760,"y":1020,"wires":[[]]},{"id":"eb5d222becc3522b","type":"ui_button","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","group":"5851d6200ca81d40","order":1,"width":0,"height":0,"passthru":false,"label":"Refresh","tooltip":"","color":"","bgcolor":"","icon":"","payload":"","payloadType":"str","topic":"topic","topicType":"msg","x":220,"y":880,"wires":[["2459acaa8e49e279"]]},{"id":"38e3e6f23b0fc946","type":"ip-location-lite","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","inputField":"payload","outputField":"payload","x":690,"y":800,"wires":[["aedc78b740f89677"]]},{"id":"aedc78b740f89677","type":"switch","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","property":"payload","propertyType":"msg","rules":[{"t":"null"},{"t":"empty"},{"t":"else"}],"checkall":"true","repair":false,"outputs":3,"x":850,"y":800,"wires":[[],[],["12546369696342e6"]]},{"id":"f857c585aa7661f8","type":"function","z":"3761db287decc539","g":"ae949abd73ceac19","name":"","func":"var k = `netplay/clients ${msg.data.hash}`\nvar v = JSON.stringify(msg.payload)\nmsg = {}\nmsg.payload = [ k, v ]\nreturn msg\n","outputs":1,"timeout":"","noerr":0,"initialize":"","finalize":"","libs":[],"x":1160,"y":740,"wires":[["e383d4f6430a364b"]]},{"id":"5851d6200ca81d40","type":"ui_group","name":"Netplay","tab":"82e08e3f65590d1c","order":4,"disp":true,"width":"24","collapse":false},{"id":"331ec98c048042f6","type":"mqtt-broker","name":"iot.internal","broker":"iot.internal","port":"1883","clientid":"","autoConnect":true,"usetls":false,"compatmode":false,"protocolVersion":"4","keepalive":"60","cleansession":true,"autoUnsubscribe":true,"birthTopic":"","birthQos":"0","birthPayload":"","birthMsg":{},"closeTopic":"","closeQos":"0","closePayload":"","closeMsg":{},"willTopic":"","willQos":"0","willPayload":"","willMsg":{},"userProps":"","sessionExpiry":""},{"id":"4475d6f04474e5ef","type":"redis-config","name":"docker","options":"{\"port\":6302,\"host\":\"docker.lan\"}","cluster":false,"optionsType":"json"},{"id":"82e08e3f65590d1c","type":"ui_tab","name":"Arcade","icon":"dashboard","disabled":false,"hidden":false}]
For the contact, copyright, license, warranty and privacy terms for the usage of this website please see the contact, license, privacy, copyright.