Table of Contents
Shortnote
Since Apple has not released an update for OSX users that are still lagging behind on Snow Leopard and below, we can use the following method to hijack the idisk connection in order to run our own cloud system using the built-in MobileMe features of Snow Leopard and below.
Procedure
We will set-up a DNS override so that idisk.me.com will resolve to a local HTTP server with WebDAV capabilities.
Requirements
The requirements are a router or a gateway with the following capabilities:
- apache2
- mod_webdav
- mod_auth
- dnsmasq
- iptables
We will be using the Debian Linux distribution as an example but the same procedure will apply to any other distribution.
dnsmasq
First we configure dnsmasq on the gateway to hijack the connection to idisk.me.com and idisk.mac.com and redirect it to our gateway.
dnsmasq uses /etc/hosts in order to serve local DNS requests. We will add a line to /etc/hosts and redirect all requests to idisk.mac.com and idisk.me.com to a local server at 192.168.1.1.. We thus need to add the following entries in /etc/hosts on the router:
192.168.1.1 idisk.me.com 192.168.1.1 idisk.mac.com
and then we restart dnsmasq so that it populates its cache with new entries.
iptables
For an extra layer of protection, we hijack all connections to akamaiedge.net and re-route them to the server at 192.168.1.1. We can do this using the iptables iprange module, although knowing the servers precisely might be a better option.
Thus, on the server, we add the firewall rule:
iptables -t nat -A PREROUTING -i eth0 -p tcp -m iprange --dst-range 23.63.233.1-23.63.233.254 -j DNAT --to 192.168.1.1
where eth0 is the internal, lan interface and 192.168.1.1 will be the webdav server with apache. The 23.63.233.1-23.63.233.254 range should cover akamaiedge.net including idisk.mac.com and idisk.me.com.
After the DNS set-up and testing is complete, the rule may be removed and one would rely only on dnsmasq to remap the DNS records. akamaiedge.net seems to serve multiple websites such as facebook.com and even apple.com, so that this rule should be eliminated after the DNS hijack works properly.
apache
The preference of apache over lighttpd is that currently lighttpd's webdav support seems to be buggy. We will thus configure an apache server to listen on 192.168.1.1 and port 443 to serve requests for iDisk clients.
Setting-up Directories
We are going to create the document root under:
/var/www/idisk/
so that users are going to be placed under the idisk directory. For example, a user called merlin will have their iDisk at:
/var/www/idisk/merlin
The password file will be at /var/www/idisk/passwd.dav and we can generate password using htpasswd. For example, we can generate a password for the user merlin by issuing the command:
htpasswd -c /var/www/idisk/passwd.dav merlin
which will ask for a password. Any other users will be added the same way.
Enabling Modules
We need to enable the following modules:
- dav
- dav-fs
- ssl
DAV
In Debian, DAV can be installed by issuing:
a2enmod dav a2enmod dav-fs
SSL
In Debian, SSL can be installed by issuing:
a2enmod ssl
Next, we need to generate a self-signed certificate for HTTPS in order to allow OSX iDisk clients to authenticate:
openssl req $@ -new -x509 -days 365 -nodes -out /etc/apache2/apache.pem -keyout /etc/apache2/apache.pem
which will ask a series of questions. The only important part is the common name which should be set it idisk.mac.com. That is, when the above command asks for:
Common Name (eg, YOUR name) []:
you should enter idisk.mac.com.
Finally, the certificate will be placed at /etc/apache2/apache.pem and we change the permissions with chmod 600 /etc/apache2/apache.pem.
Configuration File
Now we need to create a virtual host for apache so that it will handle requests to idisk.mac.com.
Ports
The ports can be changed on a Debian system by editing /etc/apache2/ports.conf so that we have:
NameVirtualHost 192.168.1.1:443 # Listen 80 <IfModule mod_ssl.c> # If you add NameVirtualHost *:443 here, you will also have to change # the VirtualHost statement in /etc/apache2/sites-available/default-ssl # to <VirtualHost *:443> # Server Name Indication for SSL named virtual hosts is currently not # supported by MSIE on Windows XP. Listen 443 </IfModule>
as you can see, we have commented out port 80 and we listen only on 192.168.1.1 because we are going to use this apache server solely for iDisk.
Virtual Host
Now we can configure the virtual host so that it listens on port 443 and on the local 192.168.1.1 address. Under Debian, this can be done by editing /etc/apache2/sites-available/default and replacing it with the following contents:
<VirtualHost 192.168.1.1:443> SSLEngine on SSLCertificateFile /etc/apache2/apache.pem ServerAdmin steve@reem.jobs DocumentRoot /var/www/idisk <Directory /var/www/idisk/merlin/> Options Indexes MultiViews AllowOverride None Order allow,deny allow from all </Directory> Alias /merlin /var/www/idisk/merlin <Location /merlin> DAV On AuthType Basic AuthName "webdav" AuthUserFile /var/www/idisk/passwd.dav # IMPORTANT IMPORTANT IMPORTANT # Require valid-user </Location> ErrorLog ${APACHE_LOG_DIR}/error.log # Possible values include: debug, info, notice, warn, error, crit, # alert, emerg. LogLevel warn CustomLog ${APACHE_LOG_DIR}/access.log combined </VirtualHost>
A crucial line to note here is the following:
# IMPORTANT IMPORTANT IMPORTANT # Require valid-user
this will make apache NOT require a valid user. Intuitively, what happens is that the OSX Finder webdav client does not authenticate every single time the iDisk is mounted. Thus, even if you mount the iDisk once and then unmount it, the second time you try to mount the iDisk, you will get a 401 from apache indicating that the client has not authenticated.
This line covers that case and is less secure, thus you should be running this system for the local network only (192.168.1.1). Disabling the authentication option is not feasible because the OX Finder icon will want at some point to authenticate with apache.
If we want additional iDisk users, we can add new aliases and new directories. For example, if we want to add another user called chickadee, we first create the directory /var/www/idisk/chickadee and then add a new alias in the virtual host configuration file:
Alias /chickadee /var/www/idisk/chickadee <Location /chickadee> DAV On AuthType Basic AuthName "webdav" AuthUserFile /var/www/idisk/passwd.dav Require valid-user </Location>
OSX
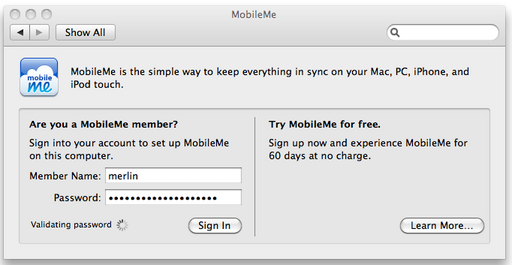
Finally, we can configure iDisk on the OSX client by going to System Preferences -> MobileMe and entering the username and password that you have configured above for webdav:
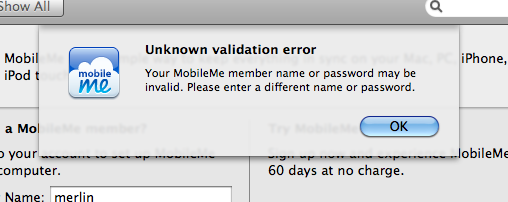
And pretty soon you will get a complaint which you can ignore:
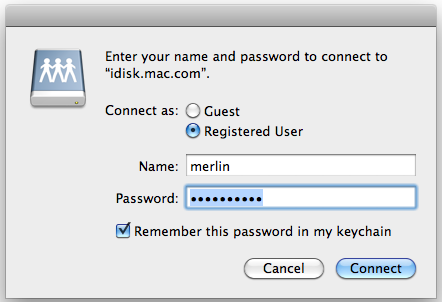
Ignore that error, press Ok and exit the system preferences. Next, go to Finder and click on the iDisk drive. If the DNS hijack is correct, you will get a prompt:
If you get an authentication error, most likely you either have:
- Not commented out
Require valid-userfor the webdav share (see apache setup). - DNS is not set-up correctly and you are connecting to
akamaiedge.net(see DNS setup).
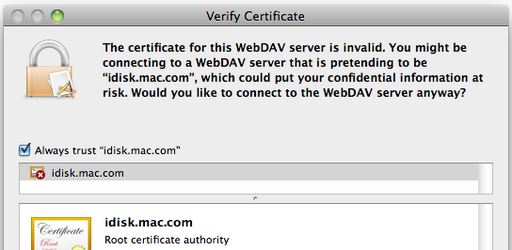
Otherwise, you will get the certificate prompt because the certificate is self-signed:
And instead of just accepting, press the details button and tick the Always trust "idisk.mac.com" box so that you will not be prompted every time you connect to iDisk.
If all goes well, you will soon find a usable iDisk that makes a great drive to transfer files between computers on your local network.
If you have followed the instructions, by now you should be able to disable the iptables rule.
Further Developments
- When you transfer files to iDisk, they will be placed on your server at
/var/www/idisk/merlin, for the usermerlin. Nothing stops you to specify a path so that the iDisk resides on some large external storage. All you would need to do is change the path to your mounted drive and it should work fine.
For the contact, copyright, license, warranty and privacy terms for the usage of this website please see the contact, license, privacy, copyright.