Table of Contents
About
There are many VPN solutions for Linux servers, amongst which we find pptp which is sort-of an adaptation of ppp dialup over ethernet. On the lower levels, pptp uses GRE and ppp, the authentication scheme being MS CHAP v2 which is considered entirely broken from a security perspective. If you are looking for a secure VPN, you may need to install OpenVPN or similar but pptp is useful as say, an alternative to Hamachi when you are not really seeking a secure transmission but rather a way to join a network over the Internet.
Setup
First, to configure a pptp server, you must install pptpd, which can be done on Debian by issuing as root:
aptitude install pptpd
which will pull-in the required packages. Next, we edit /etc/pptpd.conf:
- pptpd.conf
option /etc/ppp/pptpd-options logwtmp localip 192.168.2.1 remoteip 192.168.2.50-100
which will give the server the point-to-point address 192.168.2.1 and then it will create a pool of 50 addresses ranging from 192.168.2.50 to 192.168.2.100 for connecting clients. If you want, this pool of addresses will be dished out in a similar manner to DHCP to connecting pptp clients.
The next step is to configure the /etc/ppp/pptpd-options as specified in the previous file we edited in order to contain the following:
- pptpd-options
name pptpd refuse-pap refuse-chap refuse-mschap require-mschap-v2 require-mppe-128 ms-dns 192.168.2.1 ms-wins 192.168.2.1 proxyarp nodefaultroute lock nobsdcomp lcp-echo-failure 10 lcp-echo-interval 60
The important settings here are the following:
refuse-pap refuse-chap refuse-mschap require-mschap-v2 require-mppe-128
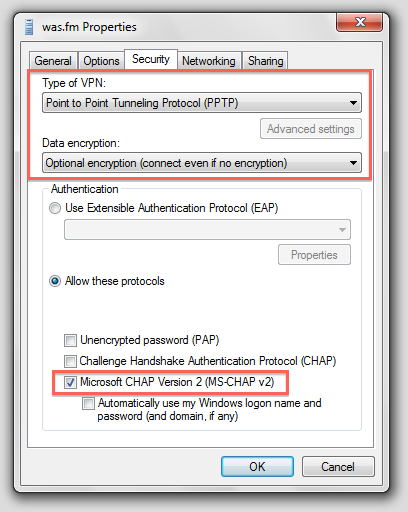
which disable the PAP, CHAP and MS CHAP v1 and enable MS CHAP v2 and MPPE 128 encryption. Let's go through them:
PAPis the plaintext authentication protocol, meaning that connecting clients will send the password over the Internet in plaintext.CHAPis a challenge authentication protocol that does not support encryption.MS CHAP v1is a challenge authentication protocol created by Microsoft that also does not support encryption.
Lastly we have MS CHAP v2 which is so far, the most supported authentication protocol by Windows, Linux, OSX and various other router hardware. A nice feature to have is MPPE 128 which is a 128-bit encryption algorithm that encrypts the data between the client and the server. Again, even with encryption, MS CHAP v2 is considered broken and given a sufficient amount of captured data, it is possible to recover passwords and observe the traffic.
Since we have pptpd configured, we can now create some secrets by editing /etc/ppp/chap-secrets. Note that we have selected MS CHAP v2 which is still CHAP so we edit /etc/ppp-chap-secrets instead of /etc/ppp/pap-secrets.
- chap-secrets
# client server password ip addresses sleepwalk * mypass * wichneyhouston * secret *
The important fields are in the first column and represent the log-in and the third column that represent the password. The configuration is now complete.
Starting the Server
To start the pptpd daemon, issue the command:
service pptpd restart
which will start pptpd in the background.
Configuring the Firewall
The firewall must be configured to allow the GRE protocol, by issuing the command:
iptables -A INPUT -p 47 -j ACCEPT
and then to allow incoming connections to port 1723 which is the port that pptpd is listening on:
iptables -A INPUT -p tcp --dport 1723 -m state --state NEW \ -m hashlimit --hashlimit 5/sec --hashlimit-burst 10 \ --hashlimit-mode srcip --hashlimit-name pptp_dos -j ACCEPT
The iptables rule allows incoming connections on port 1723 and limits the amount of initial connections to 5 per seconds with a burst of 10 per second by source-ip. This is some minor DOS protection for pptp.
Configuring Clients
In order to configure the Windows VPN, first create a new VPN and fill out the prompts - Windows will attempt to connect to the VPN using SSTP which will not work. Thus, we need to get to Adapter Settings and choose properties on the connection:
After that, proceed to the protocol settings and make the highlighted adjustments:
The last setting is to not route all the traffic via the VPN connection: